PAYROLL+
We’re more than just payroll. PPS provides a powerful web-based payroll solution PLUS integrated modules to streamline payroll operations while enhancing flexibility, security, and control.
TIME & ATTENDANCE
A built-in, robust time and attendance solution that is ready to go in our top of the line software system. It’s never been easier to track and manage your employees’ time.
THE PPS DIFFERENCE
Customer service is at the heart of our business.
We have celebrated over 20 years as a family business – and one thing has remained constant: service first. At PPS your call will never be answered by an automated message. Whether you have been a client for 1 day or 20 years, Premier Payroll Services understands the value of your time. We vow to keep customer service our priority as we have since 2000.
Read moreOUR SOLUTION
Powerful, flexible, and customized for you.
With the latest Payroll, Time & Attendance, and HR solutions that are customizable to your business, Premier Payroll provides our 1300+ clients access to a web-based, cutting edge software provider that serves over 4 million employees nationwide. Options are tailored to the needs of each customer and each one is walked through every aspect along the way.
LEARN MORE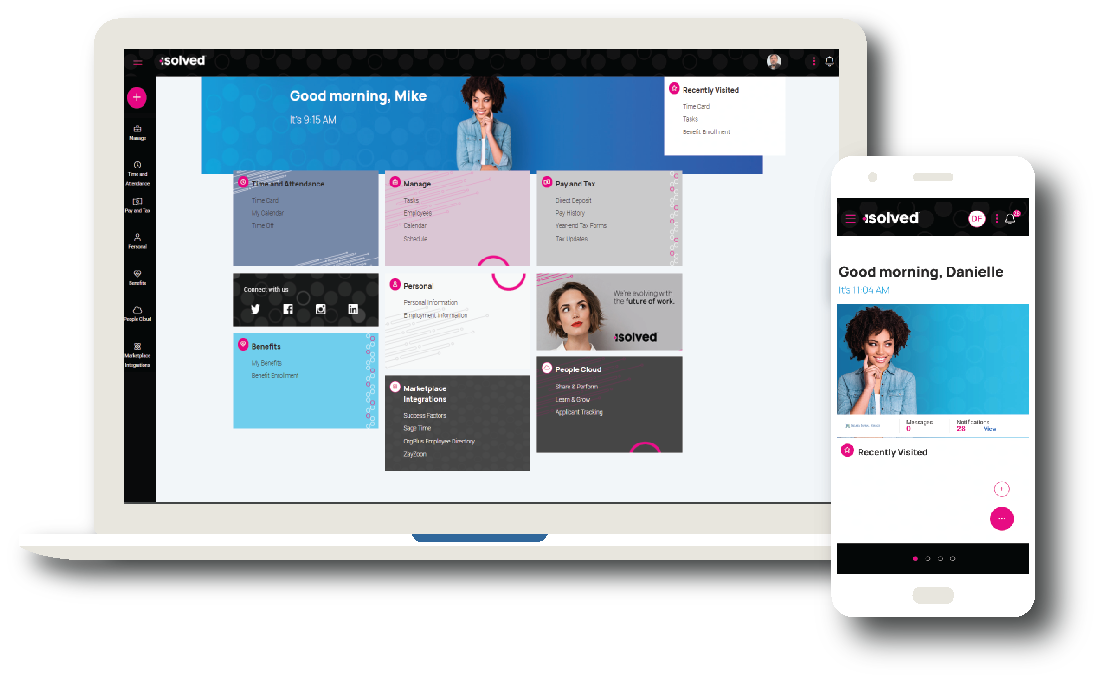
Client Testimonials
Don’t take our word for it – here’s what our clients say:
Premier Payroll has been doing our payroll for a few months now, and I couldn’t be happier. I have used the larger payroll services previously and they were a lot more money and less personal service. Premier is top notch. Everyone you speak with is knowledgeable, helpful and friendly. I really appreciate all the times I’ve called needing payroll help and information. They have the best customer service around. Thank you, Premier Payroll!
Michelle, President
MK2 Communications, LLC
We made the decision to move our business to Premier Payroll Services in September of 2019 and couldn’t be happier! Prior to moving to Premier, our experience with a national provider had left us with difficulty resolving issues and very little direct contact. The staff at Premier Payroll Services has been just the opposite! Easy to contact and always ready to help. I would recommend Premier Payroll Services to anyone who’s looking for that company that goes the extra mile.
Marie
Jeff’s Automotive
I have worked with many payroll companies over the years – both large and small and the customer service from Premier Payroll is the best. One gets an actual person on the phone immediately. I am thrilled with the knowledge and integrity of the company and with each and every employee at Premier Payroll!! Thank you for making my job easier!
Amy, CEO
Price Turner CFOS
Get back to what you do best.
Give us a call to see how we can help with trusted solutions for your small business.
GET STARTED TODAY

